The PrivacyPilot minimizes risks, ensures data protection compliance and simplifies the management of data protection-relevant processes.
The complex requirements of data protection law and information security lead to risks that are difficult to calculate, in particular fines, claims for damages, reputational damage and warnings. At the same time, this is accompanied by far-reaching documentation and verification obligations that present those responsible with major challenges. PrivacyPilot offers a user-friendly solution that minimizes risks and saves resources. The four PrivacyPilot masters are independent of each other, but can be correlated with each other in a variety of ways. The reuse of centrally maintained masters makes it possible to solve highly complex tasks with the least possible effort. The four PrivacyPilot masters form the methodological basis for semi-automated impact assessments with reliable results The needs-based linking of the masters enables an overall assessment of the level of data protection and information security. Based on this, residual risks and suitable measures to mitigate them are identified in an impact assessment. Using PrivacyPilot’s unique “flow technology”, business processes and specialist procedures can be documented in detail and subjected to a legal and technical review. The user can access our comprehensive sample templates on the marketplace. With the help of intuitive mass editing functions, users can add the desired information to selected processing activities in a targeted manner. Filter mechanisms and selection procedures allow several hundred processing activities to be edited or adapted with just a few clicks. The PrivacyPilot provides a quick and precise overview of complex structures. The risk master allows a granular risk assessment that maps both the SDM methodology required by the supervisory authorities as well as the risk assessment in accordance with BSI baseline protection or own methodologies. The flexible design of PrivacyPilot makes it possible to map even frameworks such as ISO27001 or industry-specific security standards. A risk assessment can be carried out using user-friendly matrices and the target status can be derived from this. A risk master for specific risks of an issue can be applied to several business processes and specialist procedures. The PrivacyPilot enables the time- and resource-saving definition of the target status according to recognized methods and standards. When creating TOM masters, our users can draw on extensive catalogs of pre-classified technical and organizational measures as required. They can optionally follow common standards, such as SDM, BSI, ISO or NIS-2, or an individual approach. Depending on requirements, the pre-classification of the system can be adapted to the current situation. With PrivacyPilot, you can combine the data subject perspective of data protection with the organizational perspective of information security under one roof. Use your TOM to mitigate both your data protection and information security-related risks. With PrivacyPilot, you can record your entire IT security infrastructure in one system. With an PR master, you can document the services you provide as a processor. In addition, you can register your customers as controllers in accordance with legal requirements or, alternatively, refer to your customer data management system. You can easily include your sub-processors via practical links, whereby any third country references and the legal requirements in this respect are taken into account as required. Thanks to the flexible reusability of your masters, you can also use TOM masters that have already been created elsewhere for the documentation of PR services and thus benefit from considerable synergies. PrivacyPilot enables you to document your services in a legally compliant manner – even in complex supply chains. The various master data sets, which are coordinated in their design, can be correlated with each other by PrivacyPilot. This enables robust, semi-automated risk assessments. This enables the user to obtain a comprehensive picture of all relevant circumstances relating to a processing activity, its lawfulness, the technical and organizational measures in place in this respect and the respective risk-immanent target status. As a result, the user can have the system generate a comprehensive impact assessment report – involving various responsible parties if necessary. With PrivacyPilot, you reduce your risk of fines, claims for damages, damage to your image and warnings. Data protection is essential in today’s digital world. A robust and effective data protection management system is needed to meet the many different legal requirements. PrivacyPilot offers a comprehensive solution to tool-supported optimize your existing data protection management system and improve your data protection compliance. With our software, you can effectively meet your legal accountability obligations and prove that your processes comply with legal requirements.
PrivacyPilot – the user-friendly solution
for data protection and information security
Unite separate worlds: Benefit from a symbiosis of data protection and information security.
The master concept of the PrivacyPilot
Efficient documentation and intuitive application

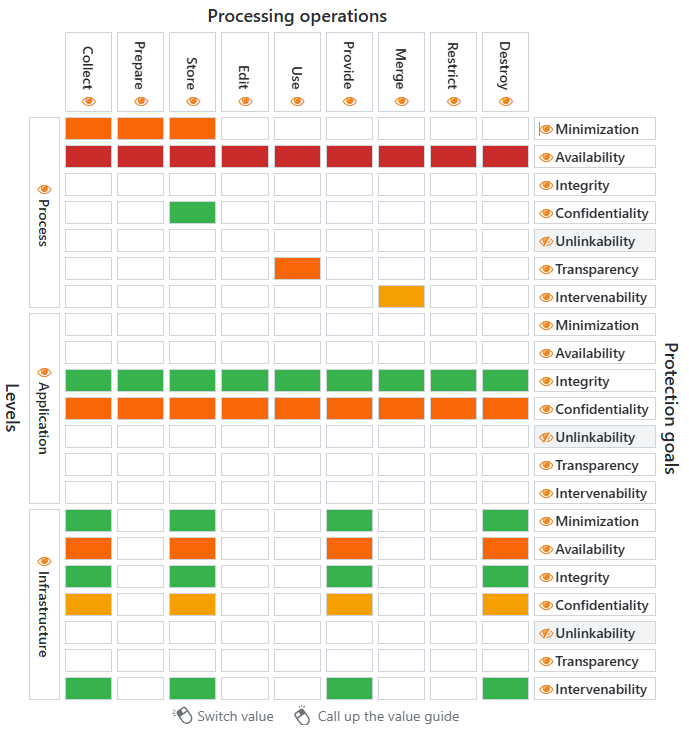
Targeted risk assessment for your risk management strategy
User-friendly TOM master for a comprehensive data security concept

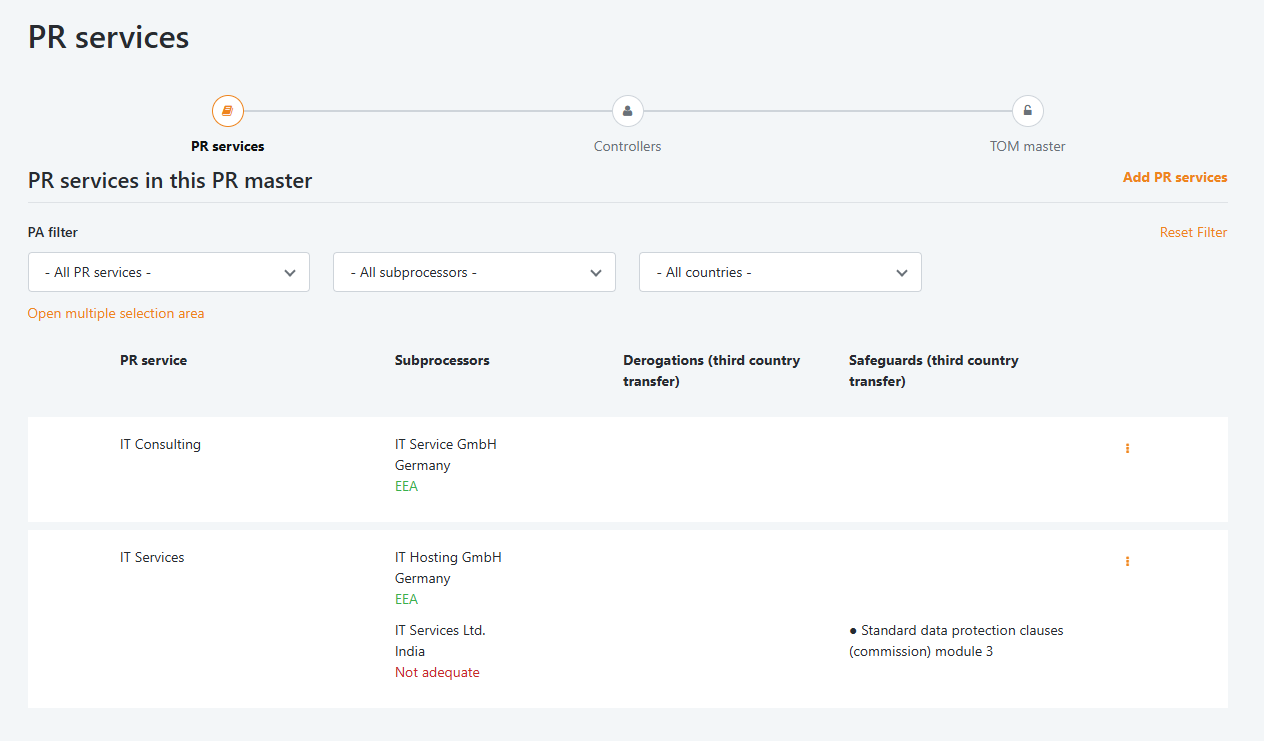
Efficient documentation of order processing
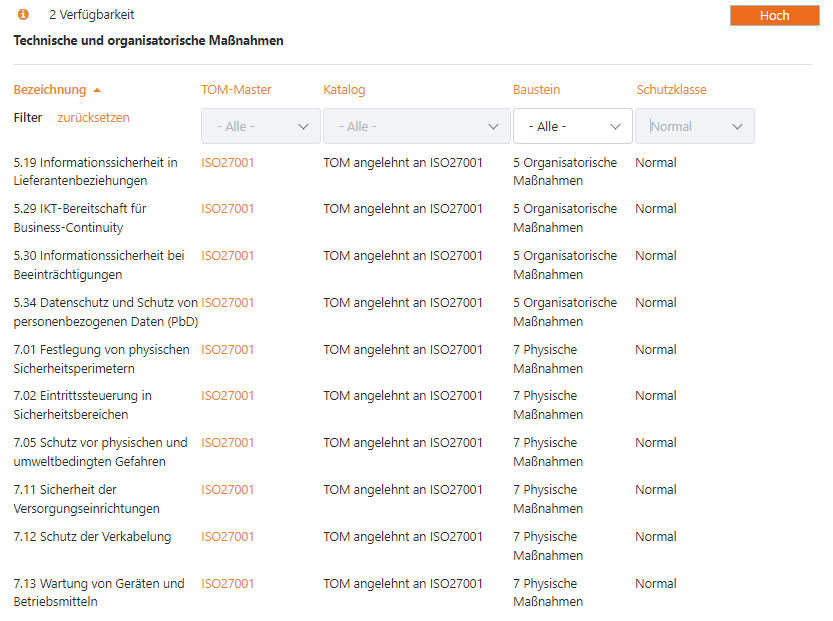
Semi-automated (data protection) impact assessment
Implement the core requirements of data protection law – quickly and easily
You can rely on our decades of expertise to ensure that your processes are legally compliant.
For example, PrivacyPilot facilitates compliance with information obligations and ensures compliance with the principle of transparency by providing clear and comprehensible information about the processing of personal data and preparing all relevant processing circumstances in a way that is appropriate for the addressee.
PrivacyPilot also facilitates the implementation of data subject rights, with practical processes significantly reducing the effort regularly required to process data subject requests. This also applies to the standardized review and further processing of data breaches.